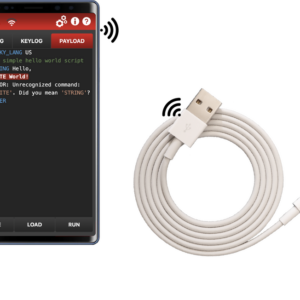
OMG USB Plug
The OMG USB Plug, also known as the O.M.G. Cable or OMG Plug, is a versatile and powerful tool used by ethical hackers and cybersecurity professionals for penetration testing and red teaming exercises. This device can emulate a variety of USB devices, including keyboards, network adapters, and storage devices, making it a valuable asset for simulating real-world attacks and testing the security of systems. Let’s delve into the details of the OMG USB Plug and explore its capabilities and uses.

Introduction to the OMG USB Plug
The OMG usb plug is a USB device that can emulate various types of USB peripherals, including keyboards, network adapters, and storage devices. This versatility allows it to be used in a wide range of penetration testing and red teaming scenarios. The device is designed to be plugged into a target computer and execute pre-programmed scripts or payloads, making it a powerful tool for simulating real-world attacks.
How It Works
The OMG USB Plug works by emulating a Human Interface Device (HID), specifically a keyboard, network adapter, or storage device. When plugged into a computer, it can send a series of keystrokes, inject network traffic, or present itself as a storage device to deploy payloads. The device is programmed using a simple, easy-to-understand language, allowing for a wide range of customization. Get your OMG + Hotplug kit at a discount now
Key Components
- Microcontroller: The brain of the device, which executes the pre-programmed scripts or payloads.
- USB Interface: Allows the device to communicate with the target computer.
- Memory: Stores the scripts or payloads that define the actions to be taken.
Capabilities and Uses
The OMG USB Plug’s versatility makes it a valuable tool for a wide range of cybersecurity tasks. Here are some of its key capabilities and uses:
- Automated Tasks: Automate repetitive tasks, such as opening web browsers, logging into systems, and executing commands.
- Payload Deployment: Deploy malicious payloads, such as backdoors, keyloggers, and ransomware.
- Data Exfiltration: Extract sensitive data from the target system.
- Network Injection: Inject malicious network traffic to exploit vulnerabilities.
- Persistence: Create persistent backdoors to maintain access to the target system.
- Evading Detection: Bypass security measures, such as antivirus software and firewalls, by mimicking legitimate USB devices.
Common Scenarios
The OMG USB Plug is particularly useful in the following scenarios:
- Penetration Testing: Simulate real-world attacks to identify and exploit vulnerabilities in a controlled environment.
- Red Teaming: Conduct advanced, adversary-simulation exercises to test an organization’s defenses.
- Social Engineering: Use in combination with social engineering techniques to gain unauthorized access to systems.
- Incident Response: Quickly deploy tools and gather evidence during incident response operations.
Creating Payloads
Creating payloads for the OMG USB Plug involves writing scripts that define the actions to be taken. These scripts can be written in various languages, depending on the specific use case. Here’s a basic example of a script that opens a command prompt and runs a command:
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
void main() {
// Open a command prompt
system("cmd.exe");
// Run a command
system("ipconfig");
// Exit the command prompt
system("exit");
}This script opens the Command Prompt, runs the ipconfig command to display network configuration details, and then exits the Command Prompt.
Key Commands
system(): Executes a command in the command prompt.cmd.exe: Opens the Command Prompt.ipconfig: Displays network configuration details.exit: Exits the Command Prompt.
Compare OMG Plug Tiers:
| O.MG Plug Tier | Basic | Elite | ||||
|---|---|---|---|---|---|---|
| Keystroke Injection (Ducky Script™) | ✔ | ✔ | ||||
| Mouse Injection | ✔ | ✔ | ||||
| Payload Slots | 8 | 50-200 | ||||
| Max Payload Speed | 120 keys/sec | 890 keys/sec | ||||
| Geo-Fencing | ✔ | ✔ | ||||
| Wi-Fi Triggers | ✔ | ✔ | ||||
| Port Stealthing | ✔ | |||||
| Self-Destruct | ✔ | |||||
| HIDX Stealth Link | ✔ | |||||
| Encrypted Network C2 | ✔ | |||||
OMG Plug Features
 Web UI over Wi-Fi
Web UI over Wi-Fi
Control everything remotely with a web browser. Desktop or mobile. Keystroke Injection
Keystroke Injection
Instant Ducky Script payloads. No recompiling or reprogramming, just click run! And with industry-leading 890keys/sec speeds. Lots of Payload slots
Lots of Payload slots
Basic model comes with 8 slots. Elite’s extra storage allows up to 200 slots! Global Keymaps
Global Keymaps
With 192 keymaps already built in, you can target machines across the world. Built in IDE
Built in IDE
The Web UI not only provides 100% of the controls but also gives you helpful feedback to catch syntax errors while rapidly building payloads. Stealth
Stealth
Spoof any USB identifier (VID/PID), extended USB Identifier, and network MAC address. Port Stealthing (Elite Models) lets the Plug stay dormant until a payload is deployed. No logs. No detections.
 HIDX Stealth Link
HIDX Stealth Link
Elite model: setup a bidirectional tunnel from Target Host > O.MG > Control Machine. Encrypted Network C2
Encrypted Network C2
Elite models: Use an encrypted connection to access & control your O.MG from anywhere. Then disable the onboard WebUI to hide and protect your O.MG on untrusted networks. Compatible with any server that runs python. Self-Destruct
Self-Destruct
Elite model: Make your legal team happy by ensuring sensitive payloads & loot are gone, and the O.MG Plug is fully inert. (recoverable with O.MG Programmer) Geo-Fencing
Geo-Fencing
Trigger payloads or other actions based on location. Keep your tool from falling out of scope! Ex: self-destruct if someone takes the O.MG Plug out of scope. Wi-Fi Triggers
Wi-Fi Triggers
Trigger payloads at long range with a single beacon.
Ethical Considerations
While the OMG USB Plug is a powerful tool, it is essential to use it responsibly and ethically. Unauthorized use of the device can result in severe legal consequences and ethical violations. Always ensure that you have explicit permission to test a system before deploying the OMG USB Plug.
Best Practices
- Authorization: Obtain written permission from the system owner before conducting any penetration testing.
- Scope: Clearly define the scope of the test to avoid unauthorized access to sensitive data.
- Documentation: Document all findings and actions taken during the test for transparency and accountability.
Conclusion
The OMG USB Plug is a versatile and powerful tool for ethical hackers and cybersecurity professionals. Its ability to emulate various USB devices and deploy payloads makes it an invaluable asset in penetration testing and red teaming exercises. However, it is crucial to use the device responsibly and ethically, ensuring that all actions are authorized and within the defined scope.
Whether you’re conducting a penetration test, simulating an advanced threat, or responding to an incident, the OMG USB Plug can be a game-changer in your cybersecurity arsenal. Stay ethical, stay legal, and stay ahead of the threats.